walking dead, It's here with intel! (zombieload)
Posted: 2019-05-17 17:58
https://www.zdnet.com/article/linux-vs-zombieload/

heheh I wont upgrade kernel anymore!!, With all of theses fixes, I think Intel CPU must be losing around 15% of performance by now.. disaster!!
spectre-meltdown-checker
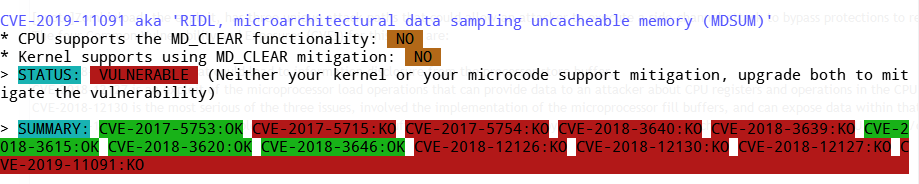
Zombieload, the exploit, has three unique attack paths that could allow an attacker to execute a side-channel attack to bypass protections to read memory. The four Common Vulnerability and Exposures (CVEs) for this issue are:
CVE-2018-12126 is a flaw that could lead to information disclosure from the processor store buffer.
CVE-2018-12127 is an exploit of the microprocessor load operations that can provide data to an attacker about CPU registers and operations in the CPU pipeline.
CVE-2018-12130 is the most serious of the three issues, involved the implementation of the microprocessor fill buffers, and can expose data within that buffer.
CVE-2019-11091 is a flaw in the implementation of the "fill buffer," a mechanism used by modern CPUs when a cache-miss is made on L1 CPU cache.
heheh I wont upgrade kernel anymore!!, With all of theses fixes, I think Intel CPU must be losing around 15% of performance by now.. disaster!!
spectre-meltdown-checker
