What could it be??.. Ive realised I was using same user password for my user and for discord, perhaps he has been able to remote hack discord password and used to take this capture?.. Ive changed my user password and set two-factor authentification in discord... Dont know, this is sometimes scary, the false security linux give you.. :
its also truth ive opera and brave browsers holded to some outdated versions (Chromium: 80.0.3987.116)..
I hope this has nothing to be with Meltdown/Spectre.. Ive those secuity holes opened cos performances reasons..:
As you can see my system is like a cheese... its has 9 holes
Spectre and Meltdown mitigation detection tool v0.43
Kernel is Linux 4.4.39-040439-generic #201612151346 SMP Thu Dec 15 18:48:20 UTC 2016 x86_64
Code: Select all
Spectre and Meltdown mitigation detection tool v0.43
Checking for vulnerabilities on current system
Kernel is Linux 4.4.39-040439-generic #201612151346 SMP Thu Dec 15 18:48:20 UTC 2016 x86_64
CPU is Genuine Intel(R) CPU 575 @ 2.00GHz
Hardware check
* Hardware support (CPU microcode) for mitigation techniques
* Indirect Branch Restricted Speculation (IBRS)
* SPEC_CTRL MSR is available: NO
* CPU indicates IBRS capability: NO
* Indirect Branch Prediction Barrier (IBPB)
* PRED_CMD MSR is available: NO
* CPU indicates IBPB capability: NO
* Single Thread Indirect Branch Predictors (STIBP)
* SPEC_CTRL MSR is available: NO
* CPU indicates STIBP capability: NO
* Speculative Store Bypass Disable (SSBD)
* CPU indicates SSBD capability: NO
* L1 data cache invalidation
* FLUSH_CMD MSR is available: NO
* CPU indicates L1D flush capability: NO
* Microarchitectural Data Sampling
* VERW instruction is available: NO
* Enhanced IBRS (IBRS_ALL)
* CPU indicates ARCH_CAPABILITIES MSR availability: NO
* ARCH_CAPABILITIES MSR advertises IBRS_ALL capability: NO
* CPU explicitly indicates not being vulnerable to Meltdown/L1TF (RDCL_NO): NO
* CPU explicitly indicates not being vulnerable to Variant 4 (SSB_NO): NO
* CPU/Hypervisor indicates L1D flushing is not necessary on this system: NO
* Hypervisor indicates host CPU might be vulnerable to RSB underflow (RSBA): NO
* CPU explicitly indicates not being vulnerable to Microarchitectural Data Sampling (MDS_NO): NO
* CPU explicitly indicates not being vulnerable to TSX Asynchronous Abort (TAA_NO): NO
* CPU explicitly indicates not being vulnerable to iTLB Multihit (PSCHANGE_MSC_NO): NO
* CPU explicitly indicates having MSR for TSX control (TSX_CTRL_MSR): NO
* CPU supports Transactional Synchronization Extensions (TSX): NO
* CPU supports Software Guard Extensions (SGX): NO
* CPU microcode is known to cause stability problems: NO (model 0xf family 0x6 stepping 0xd ucode 0xa4 cpuid 0x6fd)
* CPU microcode is the latest known available version: YES (latest version is 0xa4 dated 2010/10/02 according to builtin firmwares DB v130.20191104+i20191027)
* CPU vulnerability to the speculative execution attack variants
* Vulnerable to CVE-2017-5753 (Spectre Variant 1, bounds check bypass): YES
* Vulnerable to CVE-2017-5715 (Spectre Variant 2, branch target injection): YES
* Vulnerable to CVE-2017-5754 (Variant 3, Meltdown, rogue data cache load): YES
* Vulnerable to CVE-2018-3640 (Variant 3a, rogue system register read): YES
* Vulnerable to CVE-2018-3639 (Variant 4, speculative store bypass): YES
* Vulnerable to CVE-2018-3615 (Foreshadow (SGX), L1 terminal fault): NO
* Vulnerable to CVE-2018-3620 (Foreshadow-NG (OS), L1 terminal fault): YES
* Vulnerable to CVE-2018-3646 (Foreshadow-NG (VMM), L1 terminal fault): YES
* Vulnerable to CVE-2018-12126 (Fallout, microarchitectural store buffer data sampling (MSBDS)): YES
* Vulnerable to CVE-2018-12130 (ZombieLoad, microarchitectural fill buffer data sampling (MFBDS)): YES
* Vulnerable to CVE-2018-12127 (RIDL, microarchitectural load port data sampling (MLPDS)): YES
* Vulnerable to CVE-2019-11091 (RIDL, microarchitectural data sampling uncacheable memory (MDSUM)): YES
* Vulnerable to CVE-2019-11135 (ZombieLoad V2, TSX Asynchronous Abort (TAA)): NO
* Vulnerable to CVE-2018-12207 (No eXcuses, iTLB Multihit, machine check exception on page size changes (MCEPSC)): YES
CVE-2017-5753 aka 'Spectre Variant 1, bounds check bypass'
* Kernel has array_index_mask_nospec: NO
* Kernel has the Red Hat/Ubuntu patch: NO
* Kernel has mask_nospec64 (arm64): NO
* Checking count of LFENCE instructions following a jump in kernel... NO (only 8 jump-then-lfence instructions found, should be >= 30 (heuristic))
> STATUS: VULNERABLE (Kernel source needs to be patched to mitigate the vulnerability)
CVE-2017-5715 aka 'Spectre Variant 2, branch target injection'
* Mitigation 1
* Kernel is compiled with IBRS support: NO
* IBRS enabled and active: NO
* Kernel is compiled with IBPB support: NO
* IBPB enabled and active: NO
* Mitigation 2
* Kernel has branch predictor hardening (arm): NO
* Kernel compiled with retpoline option: NO
> STATUS: VULNERABLE (IBRS+IBPB or retpoline+IBPB is needed to mitigate the vulnerability)
CVE-2017-5754 aka 'Variant 3, Meltdown, rogue data cache load'
* Kernel supports Page Table Isolation (PTI): NO
* PTI enabled and active: UNKNOWN (dmesg truncated, please reboot and relaunch this script)
* Reduced performance impact of PTI: NO (PCID/INVPCID not supported, performance impact of PTI will be significant)
* Running as a Xen PV DomU: NO
> STATUS: UNKNOWN (couldn't find any clue of PTI activation due to a truncated dmesg, please reboot and relaunch this script)
CVE-2018-3640 aka 'Variant 3a, rogue system register read'
* CPU microcode mitigates the vulnerability: NO
> STATUS: VULNERABLE (an up-to-date CPU microcode is needed to mitigate this vulnerability)
CVE-2018-3639 aka 'Variant 4, speculative store bypass'
* Kernel supports disabling speculative store bypass (SSB): NO
* SSB mitigation is enabled and active: > STATUS: VULNERABLE (Neither your CPU nor your kernel support SSBD)
CVE-2018-3615 aka 'Foreshadow (SGX), L1 terminal fault'
* CPU microcode mitigates the vulnerability: N/A
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-3620 aka 'Foreshadow-NG (OS), L1 terminal fault'
* Kernel supports PTE inversion: NO
* PTE inversion enabled and active: UNKNOWN (sysfs interface not available)
> STATUS: VULNERABLE (Your kernel doesn't support PTE inversion, update it)
CVE-2018-3646 aka 'Foreshadow-NG (VMM), L1 terminal fault'
* This system is a host running a hypervisor: NO
* Mitigation 1 (KVM)
* EPT is disabled: N/A (the kvm_intel module is not loaded)
* Mitigation 2
* L1D flush is supported by kernel: NO
* L1D flush enabled: UNKNOWN (can't find or read /sys/devices/system/cpu/vulnerabilities/l1tf)
* Hardware-backed L1D flush supported: NO (flush will be done in software, this is slower)
* Hyper-Threading (SMT) is enabled: NO
> STATUS: NOT VULNERABLE (this system is not running a hypervisor)
CVE-2018-12126 aka 'Fallout, microarchitectural store buffer data sampling (MSBDS)'
* Kernel supports using MD_CLEAR mitigation: NO
> STATUS: VULNERABLE (Neither your kernel or your microcode support mitigation, upgrade both to mitigate the vulnerability)
CVE-2018-12130 aka 'ZombieLoad, microarchitectural fill buffer data sampling (MFBDS)'
* Kernel supports using MD_CLEAR mitigation: NO
> STATUS: VULNERABLE (Neither your kernel or your microcode support mitigation, upgrade both to mitigate the vulnerability)
CVE-2018-12127 aka 'RIDL, microarchitectural load port data sampling (MLPDS)'
* Kernel supports using MD_CLEAR mitigation: NO
> STATUS: VULNERABLE (Neither your kernel or your microcode support mitigation, upgrade both to mitigate the vulnerability)
CVE-2019-11091 aka 'RIDL, microarchitectural data sampling uncacheable memory (MDSUM)'
* Kernel supports using MD_CLEAR mitigation: NO
> STATUS: VULNERABLE (Neither your kernel or your microcode support mitigation, upgrade both to mitigate the vulnerability)
CVE-2019-11135 aka 'ZombieLoad V2, TSX Asynchronous Abort (TAA)'
* TAA mitigation is supported by kernel: NO
* TAA mitigation enabled and active: NO (tsx_async_abort not found in sysfs hierarchy)
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2018-12207 aka 'No eXcuses, iTLB Multihit, machine check exception on page size changes (MCEPSC)'
* This system is a host running a hypervisor: NO
* iTLB Multihit mitigation is supported by kernel: NO
* iTLB Multihit mitigation enabled and active: NO (itlb_multihit not found in sysfs hierarchy)
> STATUS: NOT VULNERABLE (this system is not running a hypervisor)
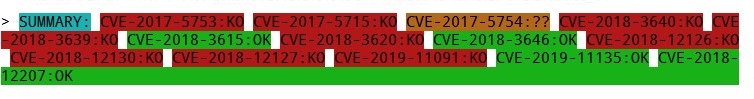
> SUMMARY: CVE-2017-5753:KO CVE-2017-5715:KO CVE-2017-5754:?? CVE-2018-3640:KO CVE-2018-3639:KO CVE-2018-3615:OK CVE-2018-3620:KO CVE-2018-3646:OK CVE-2018-12126:KO CVE-2018-12130:KO CVE-2018-12127:KO CVE-2019-11091:KO CVE-2019-11135:OK CVE-2018-12207:OK