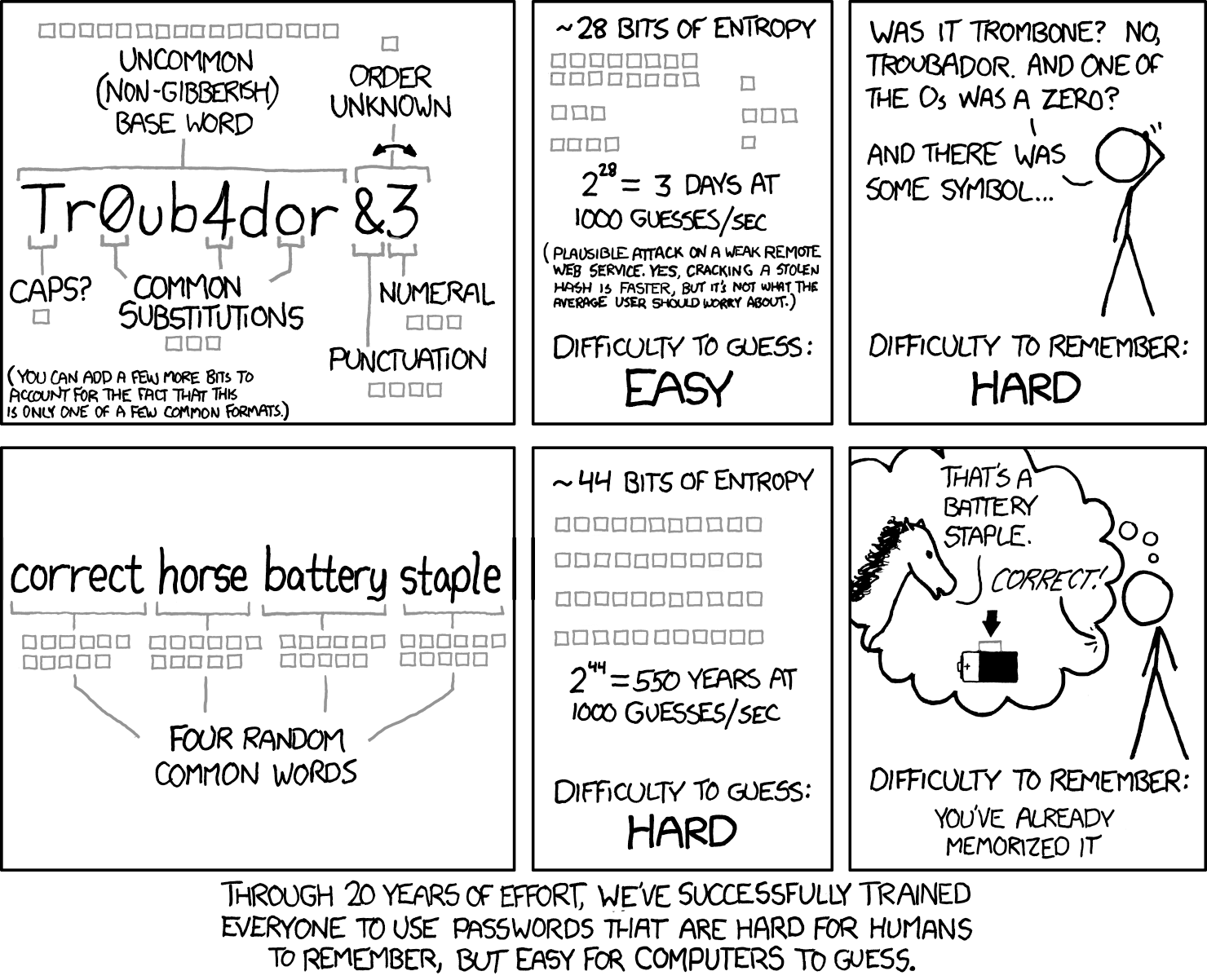
The thing is my password is very easy now, and i haven't thought about "automated connection attempts", that sounds rather... scary? My password is easy because i am not afraid of direct physical access to the computer.The root user's password should be long (12 characters or more) and impossible to guess. Indeed, any computer (and a fortiori any server) connected to the Internet is regularly targeted by automated connection attempts with the most obvious passwords. Sometimes it may even be subject to dictionary attacks, in which many combinations of words and numbers are tested as password. Avoid using the names of children or parents, dates of birth, etc.: many of your co-workers might know them, and you rarely want to give them free access to the computer in question.
But... if there is a serious network danger, then i should change my password of course. But how strong it should be? If we speak about network attacks... it should be like 32 symbols with special symbols? Or this paragraph in handbook is rather paranoid?
I have activated sudo now for my regular user. Can it (password of regular user) be less sophisticated than root password? Because it would be rather difficult to enter 32 symbols every time i wake my PC after suspend.